Fake crypto wallets: How to identify and avoid the latest scams

Crypto wallets are essential tools for storing and managing your digital assets. But as cryptocurrency adoption grows, so does the number of threat actors looking to exploit it. And a common tactic they use is the creation of fake crypto wallets.
This article will help you stay safe by teaching you how fake crypto wallets work, how to spot crypto scams, and what you should do if you’ve fallen victim to one.
How do fake crypto wallets work?
Fake crypto wallets work by impersonating legitimate digital wallets while secretly compromising your digital assets. This is typically done in one of two ways.
First, there are phishing-style scams that trick you into willingly handing over your credentials. An example is a fake wallet app that looks safe and functions just well enough to lull you into a false sense of security. But behind the scenes, any data you enter into the app or site, including your private key or seed phrase, is being transmitted to the scammer.
Second, some scams involve malware. In these cases, the fake cryptocurrency wallet contains malicious code to log your keystrokes or monitor your device in order to obtain your data or credentials.
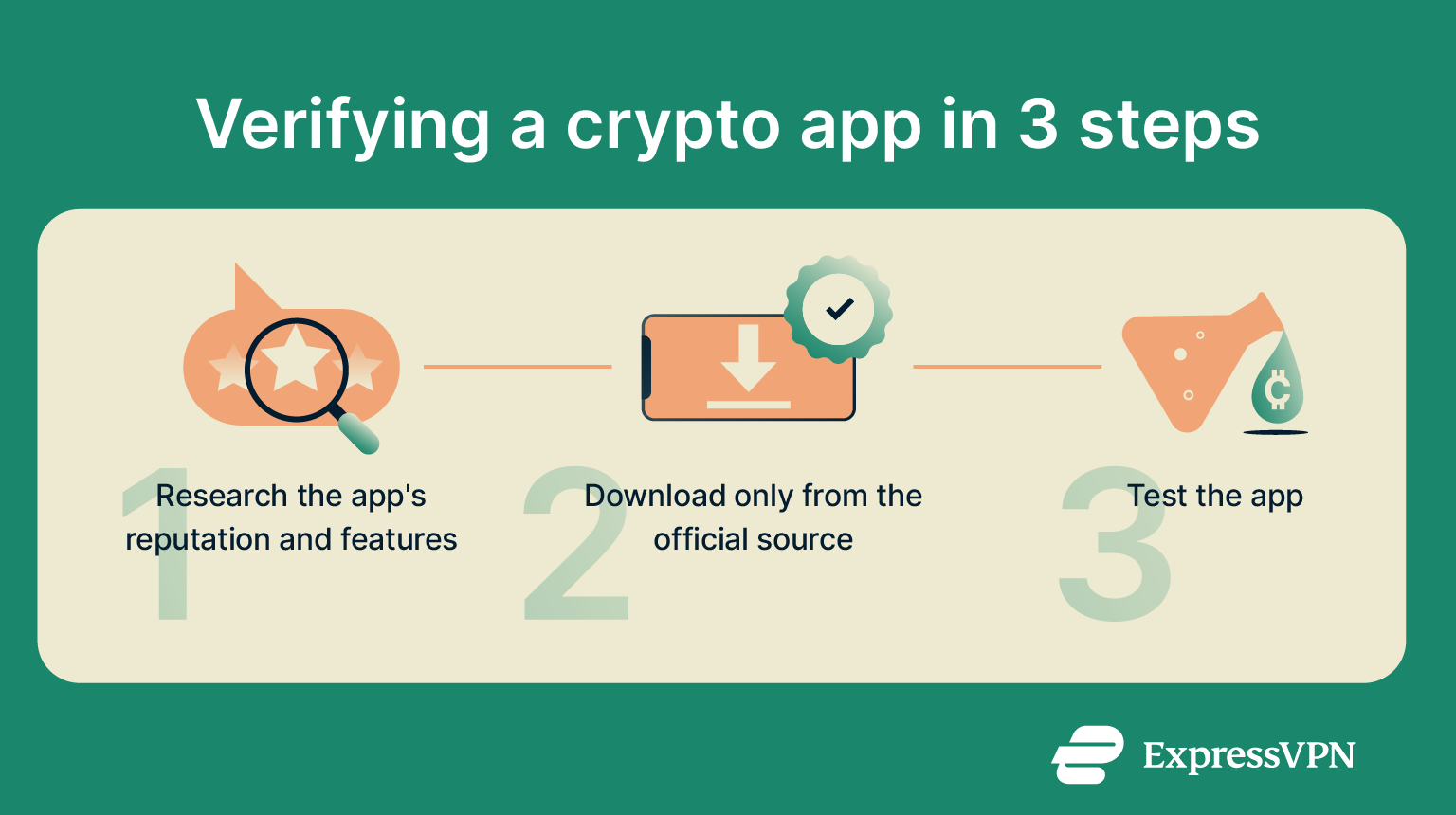
How to verify if a crypto wallet is legitimate
You should always make sure a crypto wallet is legitimate before you download and install an app and transfer funds. Here’s how.
- Download from the official source: Always download wallet apps from the official website or follow verified links from that site to the app store. While Google Play and the Apple App Store do scan and review uploaded apps, their systems aren’t foolproof. Scammers have successfully published malicious apps on both platforms in the past.
- Research the app and its developers: Check the number of downloads, investigate the developer’s reputation, and see what users are saying about the wallet app online. Legitimate crypto wallets typically have high download numbers, active community discussion, and are backed by trusted teams.
- Verify the website URL: For web-based wallets, inspect the URL character by character. Look out for typos, extra characters, or substitutions (like “.net” instead of “.com”). A common trick by scammers is to clone a site with a nearly identical domain name.
- Confirm app details before downloading: Before downloading a wallet app from an app store, ensure that the app’s name, icon, developer name, and description match those listed on the official website. This helps you identify fake apps and avoid malicious lookalikes.
- Check for transparency: Many reputable wallets are open-source (the code is made available to the public, so you’re not just taking the developer’s word on whether it’s secure or not). Others have undergone independent third-party security audits to verify their trustworthiness.
- Look for critical security features: A legitimate crypto wallet will support features like two-factor authentication (2FA), biometric login, and recovery options.
- Test with a small amount first: After performing all of the other checks on this list, but before transferring significant funds, make sure the wallet can send, receive, and recover funds as expected using a small amount of cryptocurrency.
Common fake crypto wallet scams to watch out for
Here are some common fake crypto wallet scams to watch out for so you can keep your funds safe.
Fake wallet apps in app stores
A popular scam tactic is to publish fake crypto wallet apps on official app stores like Google Play or the Apple App Store. These wallet apps often mimic the branding of trusted crypto wallets to seem more legitimate and trick users into downloading the wrong app.
To accomplish this, these apps may have a similar app icon, name, or interface. The scammer may even post fake reviews to support their disguise.
Phishing websites mimicking real wallets
Another popular tactic is to create phishing crypto wallet websites. These sites imitate the login pages or interfaces of legitimate services and often use URLs that closely resemble real ones.
Sometimes these fake sites are spread through online ads or social media posts. Other times, scammers send out phishing emails designed to create urgency. The email might claim, for example, that there’s an issue with your wallet and ask you to log in immediately to resolve the problem.
Of course, the link in the email will take you to the fake website, and any information you enter into that website will land in the hands of the scammer.
Malware-infected wallets
This type of crypto wallet scam is very similar to the first one. The scammer publishes a fake crypto wallet app. But this app doesn’t just trick you into entering your credentials; it contains malicious code that can harvest that information by logging your keystrokes and monitoring your clipboard.
Malware-infected wallets are particularly dangerous because they can compromise far more than just your crypto. Once installed, they may allow the attacker to scan your device for other sensitive information (like stored passwords or credit card details) or use your device to mine cryptocurrency, turning a crypto scam into a full-blown breach of your financial and personal data.
Real examples of fake crypto wallet scams

Case study: WalletConnect phishing site
In 2024, there were multiple scams targeting users of WalletConnect, a tool that lets you link your crypto wallet to websites and apps so you can approve transactions securely.
One of these scams involved a phishing email campaign where the threat actors posed as WalletConnect and sent users an email that contained a malicious link. This campaign also targeted other Web3 companies (built on blockchain technology), including Cointelegraph and Token Terminal. According to cryptocurrency investigator ZachXBT, the attackers were able to steal over $580,000 through this campaign.
In another scam, threat actors created a fake WalletConnect app that sent victims to a malicious website, which attempted to steal their funds. According to cyber threat intelligence company Check Point Research, this fake app was downloaded over 10 thousand times and remained on the Google Play Store for over four months.
Case study: Fake Ledger Live app for macOS
In August 2024, researchers at Moonlock Lab uncovered a fake version of Ledger Live, the official app for managing Ledger hardware wallets. The fake app was distributed using Atomic macOS Stealer (AMOS), a type of malware designed to steal sensitive data.
Attackers spread this malware through malicious code injected into compromised websites, fake software downloads, phishing emails, and deceptive links. Moonlock Lab found it on more than 2,800 compromised sites.
Once installed, AMOS harvests personal data, passwords, secure notes, and crypto wallet details before replacing the legitimate Ledger Live app with a cloned version. The fake app then displays a convincing alert about suspicious activity, prompting individuals to enter their 24-word recovery phrase.
Case study: Coinbase phishing emails
In March 2025, Bleeping Computer reported a widespread phishing campaign targeting Coinbase users.
Unlike typical phishing scams, the emails didn’t contain any malicious links. Instead, the emails directed their targets to legitimate Coinbase Wallet pages, making them appear trustworthy. The emails impersonated Coinbase support and claimed users needed to set up a new Coinbase Wallet using a recovery phrase included in the email.
By setting up a wallet with this phrase and transferring funds into it, victims were unknowingly moving their assets into a wallet the scammers controlled, allowing the attackers to steal the funds without needing access to the victims’ real recovery phrases or login credentials.
Case study: MetaMask and a surge of fake wallet apps
In June 2025, cyber threat intelligence company Cyble observed a sharp rise in fake crypto wallet apps across various app stores, identifying more than 20 fake apps. These apps often impersonated well-known wallets like MetaMask, Trust Wallet, and Phantom.
MetaMask, a popular Ethereum wallet, has been impersonated multiple times throughout the years by scammers seeking to steal user credentials and crypto assets.
In 2019, a fake MetaMask app was discovered by cybersecurity company ESET in Google Play. This app contained a strain of malware called clipper malware that would replace a copied cryptocurrency wallet address with the wallet address of the attacker, potentially tricking the user into transferring funds to the scammer.
In 2022, cyber threat intelligence company Cyble investigated the case of fake websites designed to look and function like the official MetaMask website. The download buttons for the Android and iOS apps on these sites led to malware-infected versions of the MetaMask app, which would record the victim’s seed phrase and send it to the attacker.
What to do if you’ve used a fake crypto wallet
If you suspect that you’ve fallen for a crypto scam, taking fast, informed actions can help mitigate damage. Here’s a quick rundown of what steps to take.
- Secure your remaining assets: Immediately change your passwords for associated accounts, such as linked email addresses or exchanges, and revoke permissions for connected decentralized applications (dApps). Then, transfer any remaining funds to a new, secure wallet. Enable 2FA and consider getting a hardware wallet for added security.
- Gather evidence: Take screenshots of everything: the fake wallet interface, suspicious URLs, emails, text messages, and any transaction confirmations. Record wallet addresses, transaction IDs, and timestamps. This documentation is critical for future reporting or recovery attempts.
- Report the scam: Notify the relevant wallet providers or exchanges you interacted with. While they may not be able to reverse transactions, they can flag suspicious activity or help trace funds. Then report the scam to the relevant law enforcement agency in your country. In the U.S., cryptocurrency scams are handled by the FBI Internet Crime Complaint Center (IC3).
- Consider professional help: If you lost a significant amount of crypto, it may be worth consulting a blockchain forensics firm or a crypto-savvy attorney. These experts can analyze transactions on the blockchain to trace where your funds went and potentially identify the destination wallet or exchange. In rare cases, this has helped victims recover stolen assets. But watch out for fake crypto recovery services that prey on scam victims.
Final thoughts on protecting your crypto
The crypto world is full of innovation, opportunity, and freedom, but it also comes with significant risks. In traditional finance, scams are relatively easy to avoid if you stick with established institutions. And if something does go wrong, there’s usually a fraud team ready to help.
Crypto is different. Some of the most exciting innovations come from new or lesser-known projects and technologies. Unfortunately, that’s also the kind of environment where scammers thrive. And because of how cryptocurrencies work, your options for recovery after a scam are extremely limited.
For this reason, protecting your crypto goes beyond dodging fake or insecure wallets. The key is to balance curiosity with caution. In a space where the newest opportunities can also be the most dangerous, it’s not just about having the right tools. It’s about developing good habits, asking the right questions, and approaching every new project with a healthy dose of skepticism.
FAQ: Common questions about fake crypto wallets
What are the fake crypto platforms?
Fake crypto platforms are websites or apps that impersonate legitimate cryptocurrency exchange or investment services. These platforms often mimic the look and feel of real services but exist solely to steal assets or personal data by tricking users into depositing funds, revealing private keys, or logging in with sensitive information.
Can cryptocurrency be faked?
No, real cryptocurrencies can’t be faked or forged the way fiat currencies can because blockchain technology ensures that each coin is unique and secure. However, anyone can create digital assets called “tokens” on existing blockchains. These tokens can represent anything, from money to collectibles, and are most commonly used for fundraising. Scammers often create fake tokens to trick people into buying them or sending funds.
Can I get my money back from scammer crypto?
It’s very unlikely. Blockchain transactions are easy to trace thanks to most blockchains being public ledgers, but finding a crypto wallet address is one thing, and finding its owner is an entirely different one. For this reason, you should be extremely wary of any services that claim to be able to help you recover your funds with confidence so that you aren’t made a victim of yet another scam.
Usually, the best thing you can do if you were scammed is to secure any remaining assets, contact the wallet provider or exchange involved, and report the incident to law enforcement.
What is the most trustworthy crypto wallet?
There’s no one-size-fits-all answer to this question because the most trustworthy crypto wallet depends on your needs and experience level. But here are some guidelines for avoiding shady crypto wallets and keeping your crypto secure.
Consider using a hardware wallet. This is a physical device that stores your private keys completely offline, which makes it much harder for cybercriminals to access. You might also want to choose a non-custodial wallet. This means you (not a third party) hold the private keys, so only you can access your funds.
A secure wallet should also be open-source or independently audited, have strong security features like two-factor authentication and backup recovery, and come from a provider with a good reputation.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN


















Comments
Is Gemini legit? How about a list of known scammers.